Google’s Search Console team recently sent out an email to site owners with a warning that Google Chrome will take steps starting this October to identify and show warnings on non-secure sites that have form inputs.
Here’s the notice that landed in my inbox:
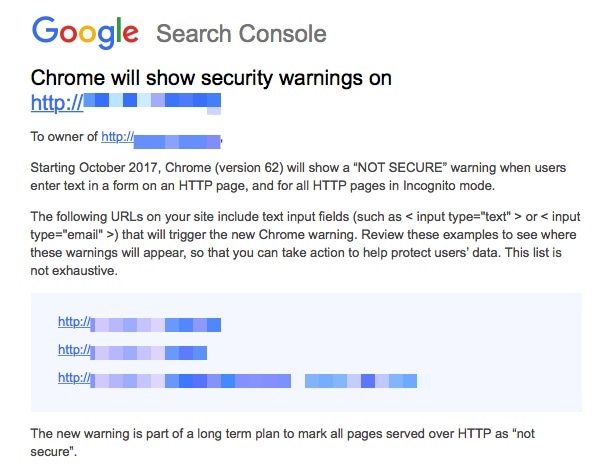
If your site URL does not support HTTPS, then this notice directly affects you. Even if your site does not have forms, moving over to HTTPS should be a priority, as this is only one step in Google’s strategy to identify insecure sites. They state this clearly in their message:
The new warning is part of a long term plan to mark all pages served over HTTP as “not secure”.
The problem is that the process of installing SSL certificates and transitioning site URLs from HTTP to HTTPS—not to mention editing all those links and linked images in existing content—sounds like a daunting task. Who has time and wants to spend the money to update a personal website for this?
I use GitHub Pages to host a number sites and projects for free—including some that use custom domain names. To that end, I wanted to see if I could quickly and inexpensively convert a site from HTTP to HTTPS. I wound up finding a relatively simple solution on a shoestring budget that I hope will help others. Let’s dig into that.
Enforcing HTTPS on GitHub Pages
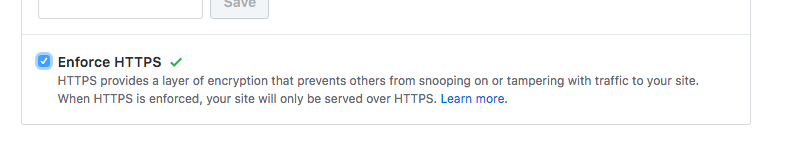
Sites hosted on GitHub Pages have a simple setting to enable HTTPS. Navigate to the project’s Settings and flip the switch to enforce HTTPS.
But We Still Need SSL
Sure, that first step was a breeze, but it’s not the full picture of what we need to do to meet Google’s definition of a secure site. The reason is that enabling the HTTPS setting neither provides nor installs a Secure Sockets Layer (SSL) certificate to a site that uses a custom domain. Sites that use the default web address provided by GitHub Pages are fully secure with that setting, but those of us that use a custom domain have to go the extra step of securing SSL at the domain level.
That’s a bummer because SSL, while not super expensive, is yet another cost and likely one you may not want to incur when you’re trying to keep costs down. I wanted to find a way around this.
We Can Get SSL From a CDN … for Free!
This is where Cloudflare comes in. Cloudflare is a Content Delivery Network (CDN) that also provides distributed domain name server services. What that means is that we can leverage their network to set up HTTPS. The real kicker is that they have a free plan that makes this all possible.
It’s worth noting that there are a number of good posts here on CSS-Tricks that tout the benefits of a CDN. While we’re focused on the security perks in this post, CDNs are an excellent way to help reduce server burden and increase performance.
From here on out, I’m going to walk through the steps I used to connect Cloudflare to GitHub Pages so, if you haven’t already, you can snag a free account and follow along.
Step 1: Select the “+ Add Site” option
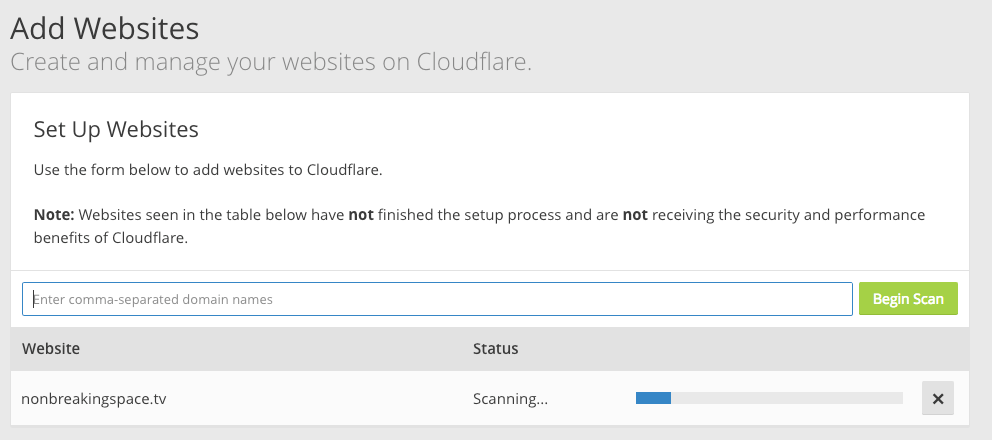
First off, we have to tell Cloudflare that our domain exists. Cloudflare will scan the DNS records to verify both that the domain exists and that the public information about the domain are accessible.
Step 2: Review the DNS records
After Cloudflare has scanned the DNS records, it will spit them out and display them for your review. Cloudflare indicates that it believes things are in good standing with an orange cloud in the Status column. Review the report and confirm that the records match those from your registrar. If all is good, click “Continue” to proceed.
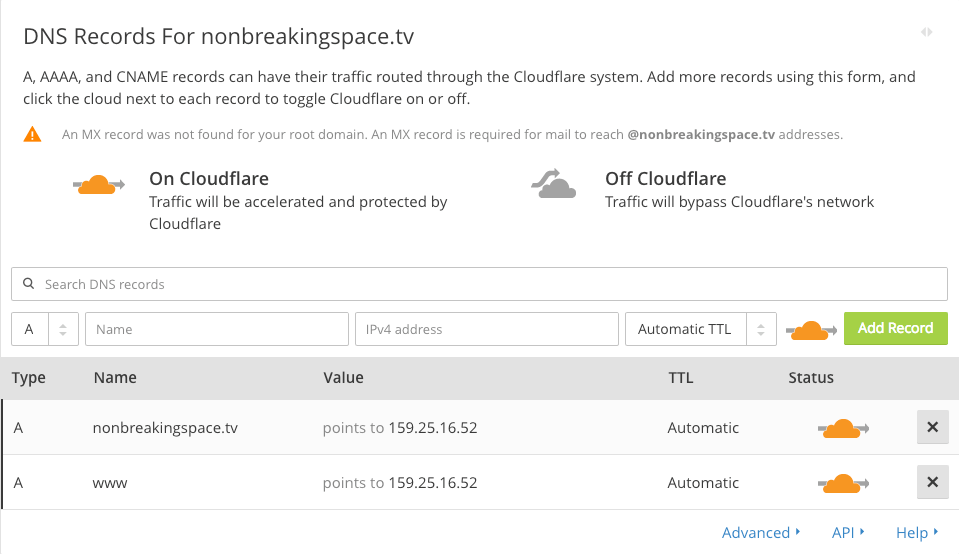
Step 3: Get the Free Plan
Cloudflare will ask what level of service you want to use. Lo and behold! There is a free option that we can select.
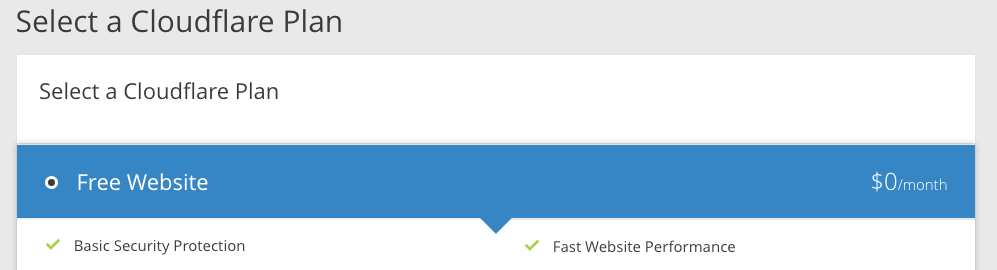
Step 4: Update the Nameservers
At this point, Cloudflare provides us with its server addresses and our job is to head over to the registrar where the domain was purchased and paste those addresses into the DNS settings.
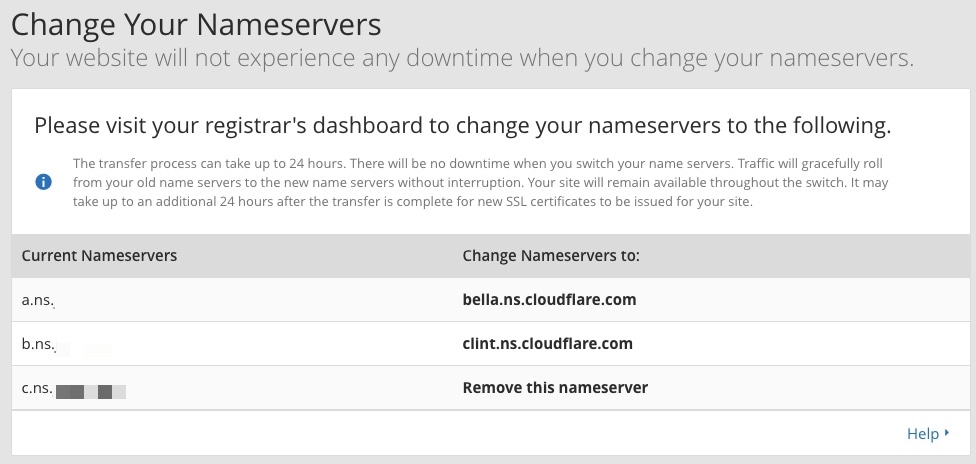
It’s not incredibly difficult to do this, but can be a little unnerving. Your registrar likely has instructions for how to do this. For example, here are GoDaddy’s instructions for updating nameservers for domains registered through their service.
Once you have done this step, your domain will effectively be mapped to Cloudflare’s servers, which will act as an intermediary between the domain and GitHub Pages. However, it is a bit of a waiting game and can take Cloudflare up to 24 hours to process the request.
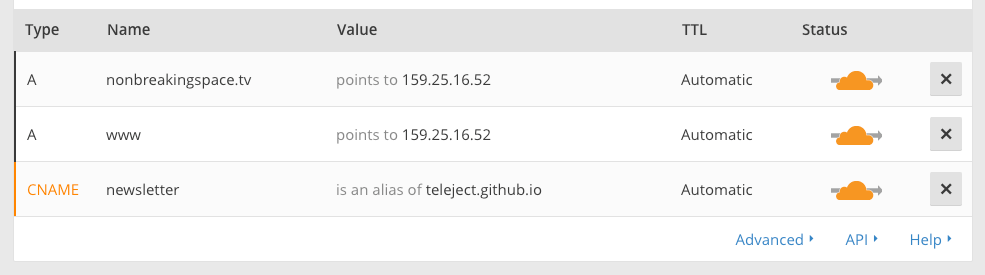
If you are using GitHub Pages with a subdomain instead of a custom domain, there is one extra step you are required to do. Head over to your GitHub Pages settings and add a CNAME record in the DNS settings. Set it to point to <your-username>.github.io, where <your-username> is, of course, your GitHub account handle. Oh, and you will need to add a CNAME text file to the root of your GitHub project which is literally a text file named CNAME with your domain name in it.
Here is a screenshot with an example of adding a GitHub Pages subdomain as a CNAME record in Cloudflare’s settings:
Step 5: Enable HTTPS in Cloudflare
Sure, we’ve technically already done this in GitHub Pages, but we’re required to do it in Cloudflare as well. Cloudflare calls this feature “Crypto” and it not only forces HTTPS, but provides the SSL certificate we’ve been wanting all along. But we’ll get to that in just a bit. For now, enable Crypto for HTTPS.

Turn on the “Always use HTTPS” option:
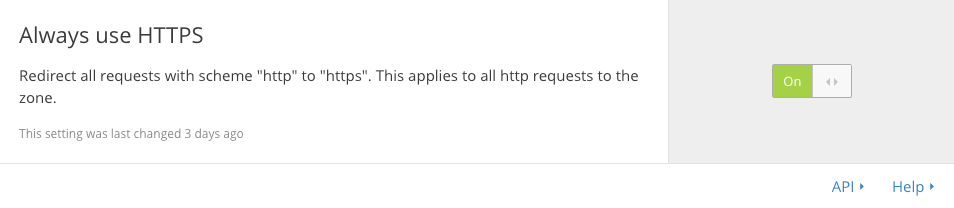
Now any HTTP request from a browser is switched over to the more secure HTTPS. We’re another step closer to making Google Chrome happy.
Step 6: Make Use of the CDN
Hey, we’re using a CDN to get SSL, so we may as well take advantage of its performance benefits while we’re at it. We can speed up performance by reducing files automatically and extend browser cache expiration.
Select the “Speed” option in the settings and allow Cloudflare to auto minify our site’s web assets:
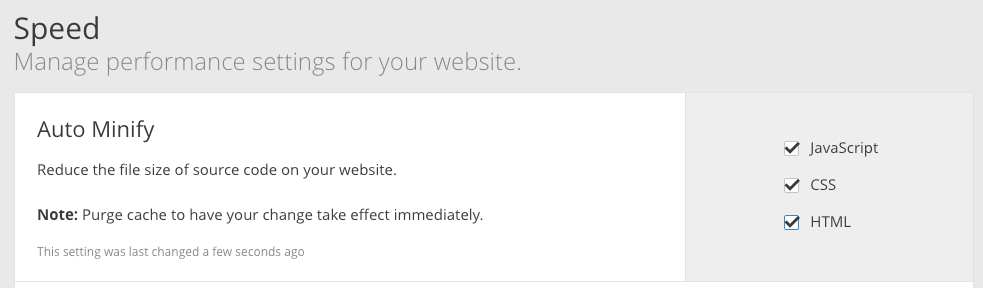
We can also set the expiration on browser cache to maximize performance:
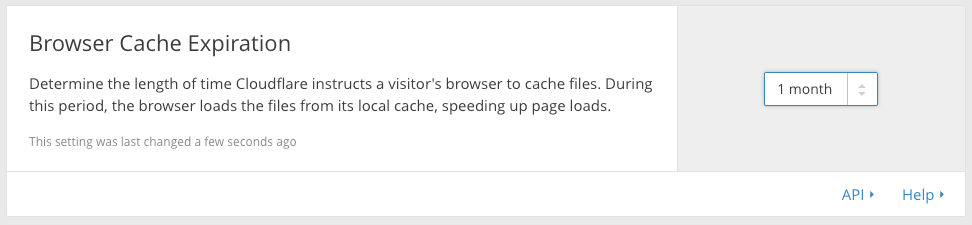
By moving the expiration out date a longer than the default option, the browser will refrain itself from asking for a site’s resources with each and every visit—that is, resources that more than likely haven’t been changed or updated. This will save visitors an extra download on repeat visits within a month’s time.
Step 7: Make External Resource Secure
If you use external resources on your site (and many of us do), then those need to be served securely as well. For example, if you use a Javascript framework and it is not served from an HTTP source, that blows our secure cover as far as Google Chrome is concerned and we need to patch that up.
If the external resource you use does not provide HTTPS as a source, then you might want to consider hosting it yourself. We have a CDN now that makes the burden of serving it a non-issue.
Step 8: Activate SSL
Woot, here we are! SSL has been the missing link between our custom domain and GitHub Pages since we enabled HTTPS in the GitHub Pages setting and this is where we have the ability to activate a free SSL certificate on our site, courtesy of Cloudflare.
From the Crypto settings in Cloudflare, let’s first make sure that the SSL certificate is active:
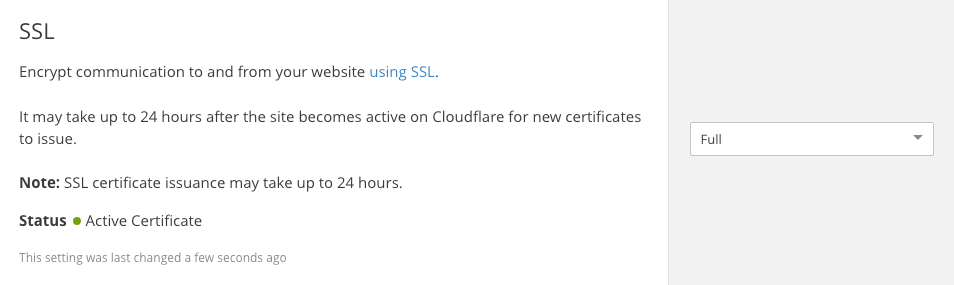
If the certificate is active, move to “Page Rules” in the main menu and select the “Create Page Rule” option:
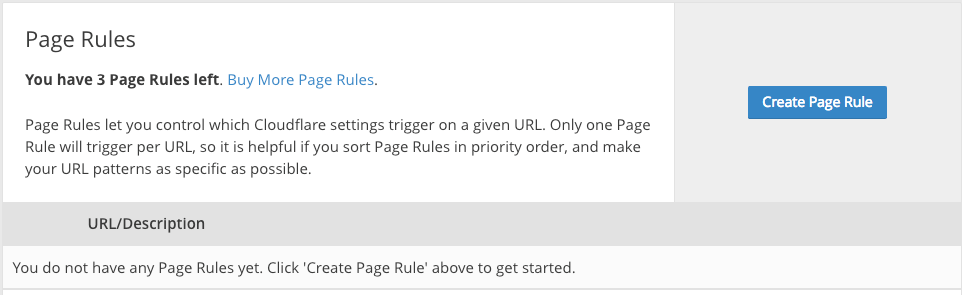
…then click “Add a Setting” and select the “Always use HTTPS” option:
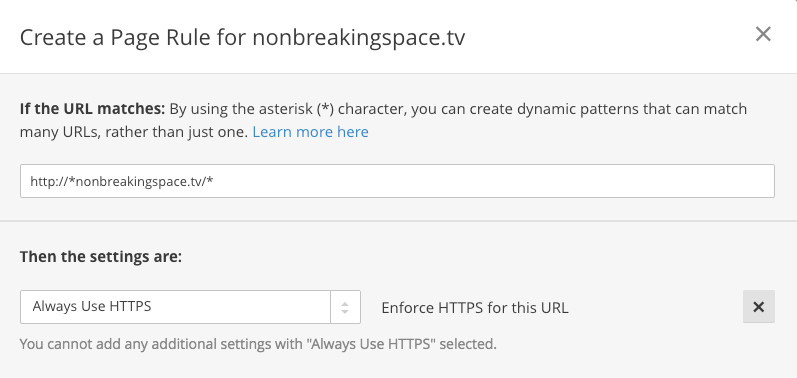
After that click “Save and Deploy” and celebrate! We now have a fully secure site in the eyes of Google Chrome and didn’t have to touch a whole lot of code or drop a chunk of change to do it.
In Conclusion
Google’s push for HTTPS means front-end developers need to prioritize SSL support more than ever, whether it’s for our own sites, company sites, or client sites. This move gives us one more incentive to make the move and the fact that we can pick up free SSL and performance enhancements through the use of a CDN makes it all the more worthwhile.
Have you written about your adventures moving to HTTPS? Let me know in the comments and we can compare notes. Meanwhile, enjoy a secure and speedy site!

This may be a silly question, but why can’t hosting/domain providers give us a 1-click (ok maybe 2-3-click) solution for this?
There are definitely hosting providers that make it a 1-click process by utilizing Let’s Encrypt. I know Siteground generates certificates automatically whenever you add a new domain to your hosting account, you don’t even have to do it yourself. I’m guessing other hosting providers have started doing that as well.
A lot of hosting providers let you install it just by clicking on one button. Here is an up-to-date list of these companies https://community.letsencrypt.org/t/web-hosting-who-support-lets-encrypt/6920
I did similar, but using Netlify.com instead of Cloudflare (https://scripter.co). These services make it painfree to switch to https, and for free too.
It’s worth noting that while using Cloudflare for SSL works and works well, it only protects traffic between Cloudflare’s servers and your visitor’s browser. Traffic from Cloudflare to your servers is not encrpyted. Any form data you’re sending back to your server would only be encrpyted as far as Cloudflare and will travel the rest of the way in the clear.
That said, I use SSL via Cloudflare here and there, we’re I’m not collecting/sending any data back to my servers.
You also may want to mention the use of a CDN for SSL in your privacy statement, if you have one online.
(I should further note that this is when using Cloudflare in front of a site that is not being served with SSL in the first place. Sorry, I wasn’t clear on that the first time around.)
Looks like in this case, you would have end-to-end SSL. Which is nifty.
(But still, update your privacy statement.)
I’m a little disturbed that you imply the use of a CDN is necessary to get an SSL certificate. It’s useful to know if you already want a CDN, but for those on the really-cheap, don’t forget about Let’s Encrypt. https://letsencrypt.org/
I didn’t get that implication, just that it was the ‘easier’ route rather than the only free route. Let’s Encrypt is wonderful, but some technical knowledge is required to get it running.
@Ken Let’s Encrypt does take a bit of knowledge to get it running. But if you’ll not be going into any sensitive data through the use of the CloudFlare CDN, then you may opt for the CloudFlare route.
But if you’ve got Let’s Encrypt through your hosting provider — by all means opt for that! I’d love to have a PCI-compliant TLS certificate any time of the day!
Kind regards,
Mic Sumner
I host some of my clients websites through a service called serverpilot.io.
On the 10$ a month plan they let you setup https+ssl using lets encrypt with a one click setup.
For the non-github pages and non-static site folks, send your developers to https://letsencrypt.org/ for free SSL. It is legit.
Why no mention of https://letsencrypt.org/ ?
Hi Christopher,
I just found this article on Twitter and it couldn’t be more timely! I was already started to panic because I thought switching to HTTPS has to be a big mess. But your solution fits like a glove (I’m already on CloudFlare).
I have a quick question though:
I have a different host (I’m located in Germany), and they don’t have an option to enforce HTTPS as you showed it for GitHub. Do you know whether checking off that box on GitHub is the same as adding this code to .htaccess file?
RewriteEngine On
RewriteCond %{HTTP_HOST} ^example.com [NC]
RewriteCond %{SERVER_PORT} 80
RewriteRule ^(.*)$ https://www.example.com/$1 [R,L]
Thanks so much in advance,
Gill
Grill, try this solution:
.htaccessRewriteEngine On
RewriteCond %{ENV:HTTPS} !on
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
I have received the same message from Google and migrated my site hosted at https://pyrx.sourceforge.io. Sourceforge makes it easy to switch with one click. Everything seems to worked fine except Disqus comments and Sumo app. For Disqus, I had to change http to https in the plugin and use Disqus dashboard to migrate the comments. Sumo app didn’t carry over likes and shares count. I’m not going to bother about that since it’s not essential for my site.
There are lots of great reasons to have a CDN, and I appreciate stepping through that process.
But if all you’re looking for is an SSL certificate, this isn’t really accurate:
SSL isn’t super expensive — it’s free. Specifically, through Let’s Encrypt, spearheaded by the EFF and Mozilla among others. Many web hosts now have it available for automatic or “one-click” installs, and in some cases it’s even the default for new websites.
Now, Let’s Encrypt provides a basic certificate, and if you have a high-value, high-traffic or very sensitive site, you may want more features in your SSL certificate, and it’s true that those options would cost money.
But if you’re going for “Switching Your Site to HTTPS on a Shoestring Budget” then it seems bizarre to not mention the really basic and really free option of Let’s Encrypt, which for most people is going to be faster to set up than Cloudflare.
I want to add a vote for https://letsencrypt.org/
This is a very real solution for everyone, even businesses to get https setup out the door.
Also, I would add that browsers are no longer using SSL actually, but TLS. (we’ve disabled SSLv2 and SSLv3 on our servers)
https://en.wikipedia.org/wiki/Transport_Layer_Security
What is the difference between SSL and TLS?
https://security.stackexchange.com/questions/5126/whats-the-difference-between-ssl-tls-and-https
I have found that calling it an “https” connection or “https certificate” helps communication between me an my clients. They understand what “https” is, but have never heard of SSL or TLS. And they can see “https” and the green lock in their browser. Then there is no need to explain either one.
We are close to a 1 click install of Let’s Encrypt (currently command line only, but one command). And there is even WordPress plugins for Let’s Encrypt.
To clarify, browsers are “planning” on removing support for SSL.
https://blog.mozilla.org/security/2014/10/14/the-poodle-attack-and-the-end-of-ssl-3-0/
Great article thanks for sharing.. I really appreciate your article… Thanks again… I created a site PocketSpider.com I will sure use https: // SSL certificate …
And any lose when I use SSL certificate on my site ?
Visitors?
Cloudflare free SSL will show warnings in all versions of internet explorer.
If you want to support all browsers then you need to use their paid plan or buy a dedicated cert from them.
I disagree, IE and Edge work absolutely fine with out any warnings for sites I’ve set up with Cloudflare free SSL
I’ve been looking to make this switch for a while, but have a question that I can’t find the answer to, maybe you guys can help me find it:
Our site is hosted remotely but with one important part of our site is using iframes to display content that is on a server here in our office. It’s my understanding that if I were to enable the https on the main site the iframes would no longer work, since the server here does not have SSL set up.
Is SSL domain based or server based?
Do I need to get SSL setup on both servers for all to function properly?
Thanks
I was pleasantly surprised at how easy it was to install Let’s Encrypt in Plesk on a Media Temple DV: https://css-tricks.com/media-temple/
I want to echo Netlify! It’s perfect (and free!) for static sites. The deploy options are super easy – you can upload via a command lien tool, hook it to a git repository (and run build scripts if necessary), or just drag and drop a static folder into their web interface. And, of course, you can enable HTTPS on custom domain names! They can manage DNS for you or you can point your own DNS records to their servers, and both options allow HTTPS.
I’d highly recommend you check out https://fly.io instead of Cloudflare. Setup is about 20 times easier, and they’re good folks.
Hi Chris Schmitt,
I agree, some hosting providers don’t have a free SSL like Let’s Encrypt, so we’ll have to opt for a CDN’s reverse proxy to account for this if the client wishes to stay on their hosting for their reasons.
But I’m pretty sure hosting providers will provide Let’s Encrypt SSL since come-on it’s everywhere and it’s great!
One Question:
Why do we choose ‘Full’, as this does not seem to work! Instead, we will have to set this to Flexible SSL please. Please review this here at CloudFlare’s SSL options.
Love Cloudflare since the website would then be able to make use of HTTP/2 protocol among other CloudFlare server enhancements — which a great thing if your current hosting provider doesn’t have these enhancements!
Kind regards,
Mic Sumner
As mentioned by Ed Zahurak, there are very serious security risks involved in relying on a CDN for security.
Remember Cloudbleed?
In other words, nobody will ever know how bad it really was, and some information (“full https requests, client IP addresses, full responses, cookies, passwords, keys, data, everything”) might still be publicly queryable.
Let’s Encrypt provides end-to-end encryption whereas Cloudflare doesn’t. So for my money (they’re both free!) it’s a more secure solution regardless of whether or not you’re sending data to your server. Hope this helps some folks decide!
Thank you for the reply Khek.
Good to know that Let’s Encrypt is now the more obvious choice!
Hope any CloudFlare staff might respond to this?
Kind regards,
Mic Sumner
One thing to note, if you are doing any kind of financial transactions you will want your site to be PCI-compliant — and so will your payment gateway. If you go the CloudFlare route, you’ll have to upgrade to their $200/month plan. But, that’s fair. You’re hypothetically making money.
Yes, letsencrypt.org should definitely be mentioned for “shoestring budget”. And “SSL” is an old acronym that shouldn’t be used because it has long since been replace by TLS which does lots of marvelous things like allowing you to apply multiple certs over a single IP! C’mon people –Get with the times!